Attackers Don’t Rush Data. They Kill Visibility First.
This attack path shows a modern sequence where the adversary first disables endpoint/XDR visibility (Defense Evasion), then uses exposed storage management-plane weaknesses for Initial Access, escalates privileges/executes remote commands, and ends with full control of FlashArray/FlashBlade—enabling exfiltration, encryption, or destruction. Vendor example is illustrative; the pattern is universal
12/22/20251 min read
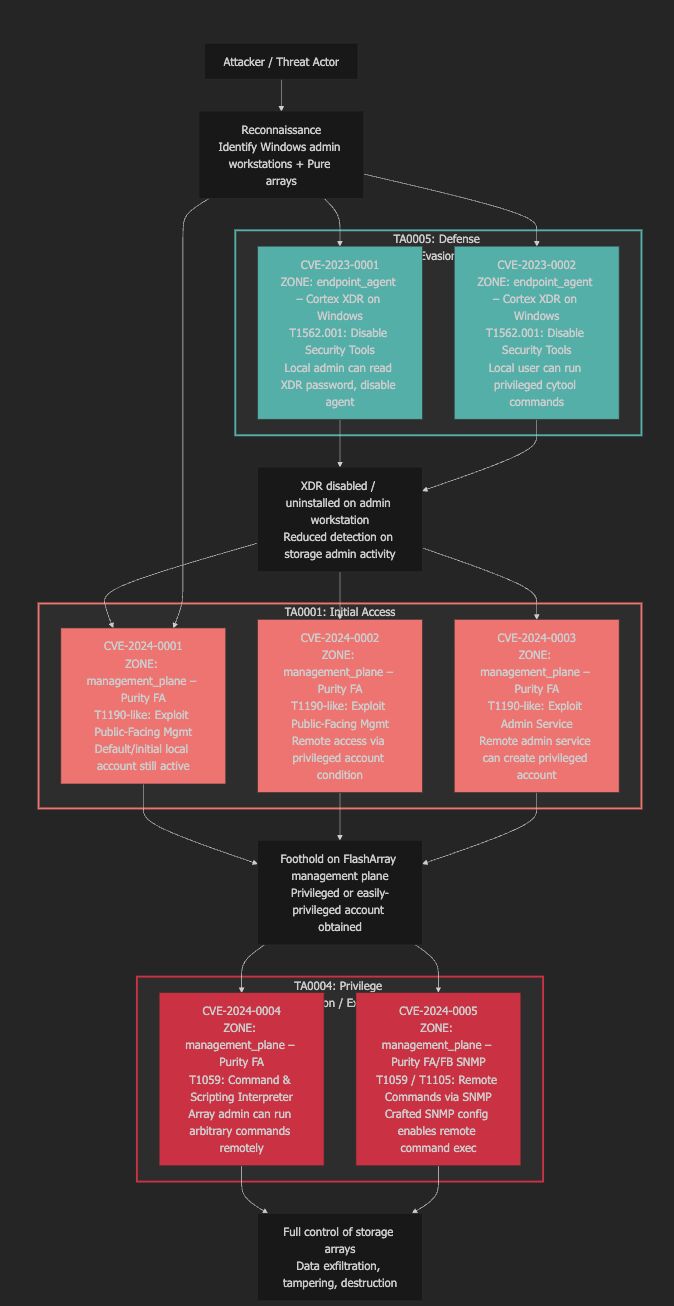
My post contentDefense Evasion Before Initial Access !!! 🚨
Modern attacks rarely begin with “malware.” They begin by removing your ability to see.
In the attack path below, the adversary doesn’t sprint toward data.
They first degrade endpoint visibility:
Local admin abuse
Defense evasion against the XDR agent
SOC telemetry weakened — quietly
Only then does the real compromise unfold:
# Exposure in the storage management plane (default/weak configurations)
# Privileged remote access
# Remote command execution
# Persistence via account backdoors
# Full control of FlashArray / FlashBlade
Defense Evasion (endpoint/XDR) → Initial Access (storage mgmt plane) → Priv Esc → Full control → Data exfiltration / encryption / destruction.
The outcome is predictable:
exfiltration, encryption, destruction.
Not because an organization lacked tools —just security was siloed by layers.
Endpoint teams assumed XDR coverage.
Infrastructure teams assumed the management plane was trusted.
No one owned the path connecting them.
This is why modernization is not:
❌ adding another product
❌ tuning CVSS thresholds
❌ building one more dashboard
Modern security is:
✅ prioritizing attack paths, not alerts
✅ treating security controls as software + privilege (therefore attackable)
✅ connecting endpoint → identity → management plane → impact
✅ fixing pivot exposures that collapse multiple paths — not chasing thousands of findings
At Chakra-ETI, we don’t ask:
“Is this CVE critical?”
We ask:
“If this fails, what fails next — and how fast do we reach impact?”
That’s the difference between visibility and proof. 😊
hashtag#CyberSecurity hashtag#AttackPaths hashtag#XDR hashtag#DefenseEvasion hashtag#SecurityModernization hashtag#CISO hashtag#SecOps hashtag#ZeroTrust hashtag#ChakraETI
Using Palo Alto CVEs here as a representative example—the point is vendor-agnostic: any high-privilege security agent/console can become a target!
Hayasis
Leading the future of cybersecurity with AI-driven solutions, comprehensive threat protection, and innovative security frameworks.
© 2025. All rights reserved.
