CVE Graphing
Most vulnerability mgmt tools still give you spreadsheets. Your adversary has attack paths.
Apparao Chandrapti
12/19/20251 min read
Most vulnerability mgmt tools still give you spreadsheets.
Your adversary has attack paths.
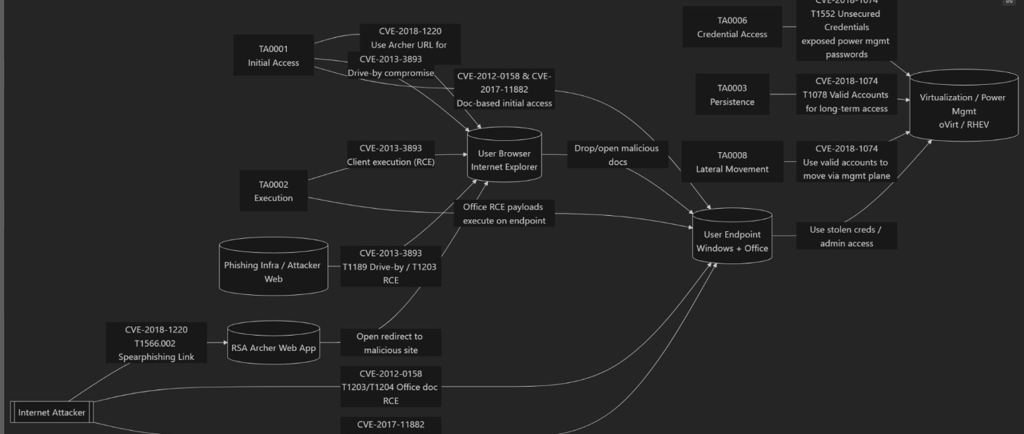
This is what Chakra-ETI gives me for a single scenario – straight from the MCP server:
Internet Attacker → RSA Archer → Phishing Infra → IE → Windows + Office → oVirt / RHEV
Every hop is backed by specific CVEs + ATT&CK tactics, not vibes.
What a CISO can see in this graph:
Business system as bait
RSA Archer Web App with CVE-2018-1220 is not “just a vuln in GRC”.
Chakra-ETI tags it as T1566.002 (Spearphishing Link): your risk platform is being used as a trusted redirector into attacker infra.
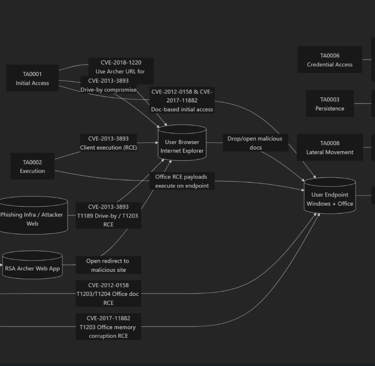
User click → browser → endpoint is fully mapped
CVE-2013-3893 (IE RCE) → TA0001 / TA0002 (Initial Access / Execution).
One click and the node becomes “User Browser – Internet Explorer”, then pivots into:
CVE-2012-0158
CVE-2017-11882
Graph view: “Browser → Office → User Endpoint (Windows + Office)”.
Single endpoint → full control plane
From that endpoint node, Chakra-ETI models:
Credential theft / token abuse (TA0006 – Credential Access).
Lateral to management plane via CVE-2018-1074
T1552 – Unsecured Credentials
T1078 – Valid Accounts
TA0008 – Lateral Movement into Virtualization / Power Mgmt (oVirt/RHEV).
Same CVE, three tactics. The graph shows all three, in context.
Crown jewel is explicit, not implicit
The right-most node is “Virtualization / Power Mgmt – oVirt / RHEV”: your hypervisor control plane.
Once that’s red, every VM, every workload underneath is effectively compromised.
When we show this view to a CISO, the discussion is no longer:
“Why haven’t you patched CVE-2012-0158 yet?”
(TO)
“This single endpoint chain gives a remote actor a straight line to your virtualization control plane.
If we fix these 3 pivot CVEs and add these 2 detections, this entire path dies.”
That’s what Chakra-ETI is doing ... 😊
hashtag#CyberSecurity hashtag#CISO hashtag#ThreatHunting hashtag#VulnerabilityManagement hashtag#CVE hashtag#MITREATTACK hashtag#AttackPath
Hayasis
Leading the future of cybersecurity with AI-driven solutions, comprehensive threat protection, and innovative security frameworks.
© 2025. All rights reserved.
