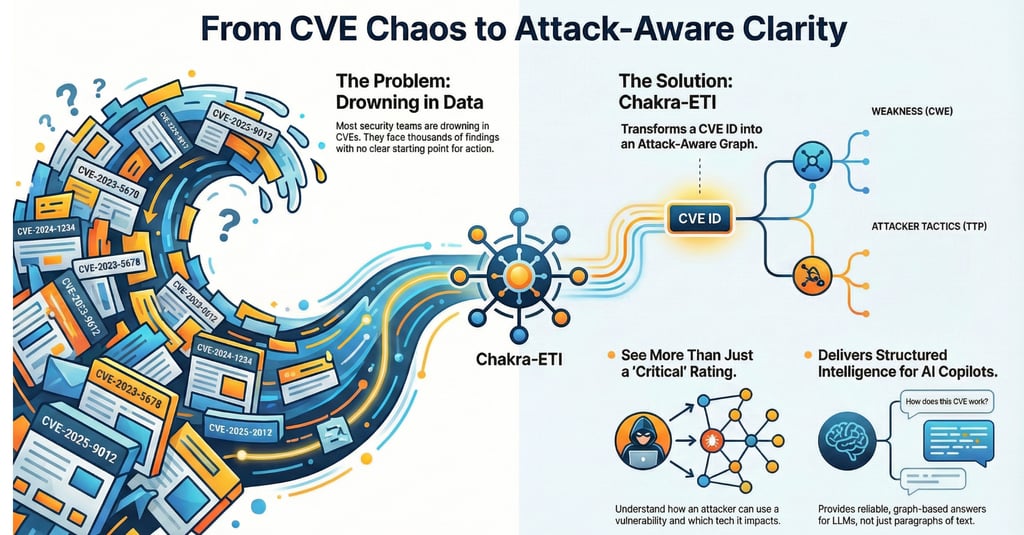
Drowning in CVEs?
Chakra-ETI turns a CVE ID into an attack-aware graph: CWE → TTPs → impact paths — so you see what matters beyond “Critical”. Less chaos. More clarity. Faster action. Want a sample on your top 20 CVEs?
12/26/20253 min read
Why vulnerability programs need context, not more “critical” tickets
Security teams aren’t short on data. They’re drowning in it.
Every scan delivers another wave of findings—thousands of CVE IDs, severity labels, and remediation notes. The list keeps growing, but the starting point stays unclear. Teams patch what looks urgent, then repeat the cycle, often without a clear answer to the one question that matters most:
Which vulnerabilities actually move us closer to a breach?
This is the gap between CVE chaos and attack-aware clarity—and it’s exactly where Chakra-ETI fits.
The problem: drowning in vulnerability data
Traditional vulnerability management tends to default to one lens: severity.
If it’s “Critical,” it goes to the top.
If it’s “Medium,” it waits.
But modern attacks don’t follow severity rankings. They follow opportunity and pathways:
what is exposed
what can be chained
what enables lateral movement
what leads to privilege escalation
what ultimately reaches business impact
So while teams are busy sorting and patching, attackers are busy connecting the dots.
The shift: a CVE ID becomes an attack-aware graph
Imagine you take one CVE ID—not a list, just one—and instead of seeing a number and a score, you see a structured map:
1) Weakness (CWE)
What kind of flaw is it, fundamentally?
Input validation? Auth bypass? Privilege escalation? Remote code execution?
CWE gives the vulnerability a “root cause” identity—useful for:
finding repeating patterns in your environment
improving secure design and controls
understanding exploit mechanics beyond the vendor label
2) Attacker tactics / techniques (TTPs)
How would an adversary actually use this flaw?
Mapping CVEs to attacker behavior changes prioritization dramatically. Instead of “critical because score,” it becomes:
critical because it supports initial access
dangerous because it enables credential access
urgent because it accelerates lateral movement
high-impact because it enables exfiltration or ransomware
This is where vulnerability data starts to align with threat hunting, incident response, and SOC operations.
3) Graph relationships
Now connect that CVE to:
impacted technology
adjacent assets
possible next steps
known exploit patterns and chaining likelihood
Suddenly, the CVE is not a ticket.
It’s a node in an attacker’s route.
That’s what “attack-aware clarity” looks like.
Why “more than just a critical rating” matters
Security teams lose time because severity isn’t action.
Two CVEs can both be “Critical,” but only one may:
sit on an internet-facing system
connect to privileged identity paths
appear repeatedly across multiple potential chains
unlock access to a sensitive business system
When you add attacker context and graph connections, prioritization becomes:
what to fix
where it matters
what it prevents
what it breaks in the attacker workflow
This reduces noise and improves speed—not by working harder, but by working smarter.
Structured intelligence for AI copilots (and humans)
Another challenge in security today is that teams want copilots and assistants, but most tools output long paragraphs or scattered links.
AI copilots work best when intelligence is structured:
CVE → CWE
CVE → TTPs
CVE → affected tech
relationships and confidence
evidence and rationale
Chakra-ETI is built to deliver that structured, graph-based intelligence so:
SOC analysts can triage faster
CTEM / vulnerability teams can prioritize rationally
CISOs can communicate risk clearly
AI copilots can reason over consistent data, not guess from unstructured text
What this unlocks in practice
When CVE management becomes attack-aware, teams typically unlock:
✅ Clear starting points
Not “fix everything critical,” but “fix the CVEs that enable the breach route.”
✅ Better cross-team alignment
Vulnerability management, threat hunting, and incident response operate on the same model: attacker behavior.
✅ Faster prioritization
Less debate, fewer false urgencies, and a fix list that actually reduces risk.
✅ Better reporting
Because risk is explained in terms of attacker steps and potential impact—not raw counts.
Closing: the future is connected
CVE lists were designed for inventory.
Modern defense requires context and connection.
Moving from CVE chaos to attack-aware clarity isn’t about adding more tools. It’s about adding the intelligence layer that transforms a CVE ID into:
weakness understanding (CWE)
attacker behavior (TTPs)
connected reasoning (graph)
That’s what Chakra-ETI is built to deliver.
Hayasis
Leading the future of cybersecurity with AI-driven solutions, comprehensive threat protection, and innovative security frameworks.
© 2025. All rights reserved.
