From Lists to Chains: A Smarter Approach to Vulnerability Management post description.
Vulnerability management is broken when “critical” means “everything.” Chakra-ETI helps you identify the few CVEs that actually unlock the attack path—and report it in framework language teams already use.
12/26/20253 min read
From Lists to Chains: A Smarter Approach to Vulnerability Management
Most vulnerability programs still run on a familiar loop: scan, export, sort by severity, patch the “critical” items, repeat. On paper, that sounds disciplined. In reality, it often produces the same outcome—large backlogs, constant firefighting, and a lingering question from leadership:
“Are we actually reducing breach risk?”
The issue isn’t that teams aren’t working hard. The issue is that traditional vulnerability management treats security as a list problem, while modern attackers operate as a chain problem.
The problem with “vulnerabilities as a list”
Scanner outputs are typically presented as an inventory:
thousands of CVEs
severity scores (CVSS)
asset names
remediation notes
This is useful for visibility, but it misses the most important part: how vulnerabilities connect.
Attackers rarely succeed because of one “critical CVE” in isolation. They succeed by chaining weaknesses together across systems and steps:
a weak entry point
a pivot into internal access
credential abuse
privilege escalation
impact (data theft, ransomware, disruption)
A list tells you what exists.
It doesn’t tell you what leads to a breach.
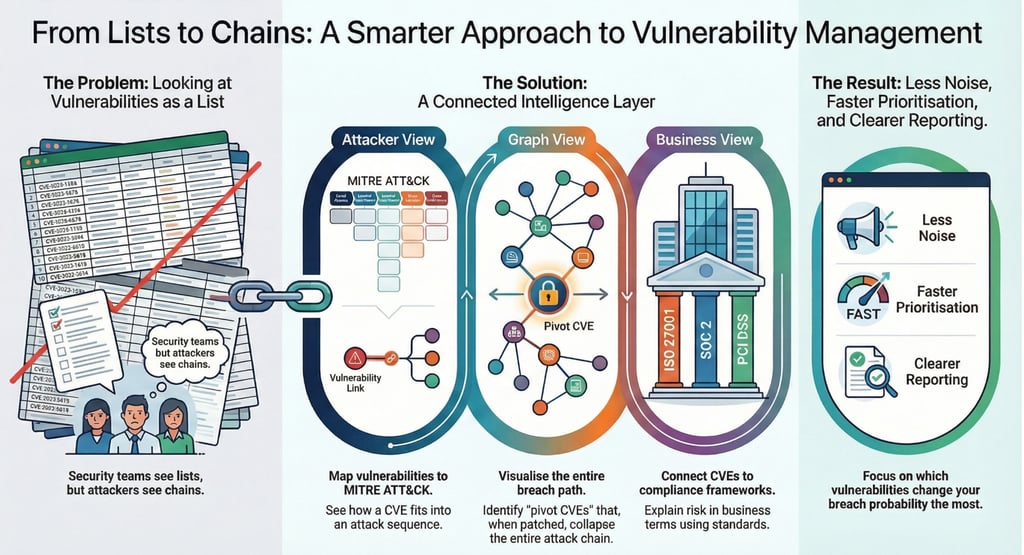
The smarter approach: a connected intelligence layer
To prioritize like an attacker, you need a layer that connects vulnerability data into real operational context. At Hayasis, we built Chakra-ETI to act as that connected intelligence layer—turning raw findings into attack-aware clarity.
This approach can be understood through three connected views:
1) The attacker view: Map vulnerabilities to MITRE ATT&CK
The first step is shifting from “what is the CVE?” to “how would an attacker use it?”
By mapping vulnerabilities to MITRE ATT&CK techniques and tactics, security teams can see where each weakness fits in an adversary workflow:
initial access
execution
persistence
privilege escalation
lateral movement
credential access
exfiltration / impact
This helps teams reason in terms of attacker intent, not just severity.
2) The graph view: Visualize the breach path
Once vulnerabilities are connected to tactics and assets, the next step is building the attack path graph.
Graphing enables teams to:
connect CVEs to affected assets and adjacent systems
visualize potential breach routes from entry to impact
identify where one weakness enables movement to the next
Instead of a thousand isolated findings, teams see a connected chain that mirrors how compromise happens in the real world.
The key value: identifying pivot CVEs
In most environments, a small number of vulnerabilities act as pivots—they appear in multiple attack chains and enable multiple next steps.
These are the vulnerabilities that:
connect systems together
unlock lateral movement
accelerate privilege escalation
increase the probability of impact
When you patch a pivot CVE, you often collapse an entire chain—not just a single ticket.
3) The business view: Connect CVEs to compliance and reporting
Security teams also face a reporting gap. Engineering wants technical clarity. Leadership wants business risk. Auditors want evidence.
A connected intelligence layer can translate technical findings into framework language and reporting-ready narratives, mapping risk to:
ISO 27001
SOC 2
PCI DSS
(and other governance requirements)
This helps explain not just what is vulnerable, but:
why it matters
what business process it affects
what risk is reduced when fixed
The result: less noise, faster prioritization, clearer reporting
When vulnerability management becomes chain-aware, teams typically experience three practical improvements:
1) Less noise
“Critical everywhere” becomes critical here—based on exposure, path position, and attacker relevance.
2) Faster prioritization
Instead of patching in severity order, teams focus on pivot vulnerabilities that collapse multiple attack routes.
3) Clearer reporting
Security outcomes can be communicated in terms of:
attack path reduction
exposure reduction
compliance-ready narratives
Why this matters now
Modern attacks are multi-stage and cross-layer. They move through identities, endpoints, cloud control planes, misconfigurations, and application weaknesses. A list-only approach struggles because it treats each finding as independent.
A chain-based approach reflects reality:
risk is not only about severity—risk is about connectivity.
How Chakra-ETI supports this approach
Chakra-ETI by Hayasis is designed to help security teams move from lists to chains by providing:
attacker-aligned mapping (MITRE ATT&CK view)
connected graphing and pivot identification
business/compliance reporting views
narrative outputs that are usable for SecOps and leadership discussions
Ready to see your vulnerabilities as chains?
If your team is drowning in CVE volume and struggling to prioritize what truly reduces breach risk, it may be time to shift the model.
Stop chasing lists. Start breaking chains.
Hayasis
Leading the future of cybersecurity with AI-driven solutions, comprehensive threat protection, and innovative security frameworks.
© 2025. All rights reserved.
